Wireless Sensor Networks Vampire Attack Defense Project
Problem Definition
Problem Description: The increasing prevalence of Vampire attacks on wireless ad-hoc sensor networks poses a significant threat to the stability and functionality of the networks. These attacks, which rapidly drain the battery power of nodes, can disrupt communication and compromise the integrity of data transmission. Current protocols are vulnerable to these attacks, as malicious insiders can easily exploit protocol compliance to carry out destructive actions. The exponential increase in energy consumption caused by a single Vampire attack can have far-reaching consequences for the network's overall performance. Therefore, there is a pressing need to develop effective solutions to detect and mitigate Vampire attacks in wireless ad-hoc sensor networks to ensure the security and reliability of data transmission.
Proposed Work
The research explores the concept of Vampire attacks in wireless ad-hoc sensor networks, focusing on the depletion of nodes' battery power by malicious entities at the routing protocol layer. These attacks, termed as Vampire attacks, are not specific to any particular protocol and have been found to be highly destructive, difficult to detect, and easy to carry out by a single malicious insider. The study reveals that all protocols are vulnerable to such attacks, which can significantly increase energy consumption in the network. Various mitigation strategies are considered, including the development of a proof-of-concept protocol to control the damage caused by Vampires during data packet forwarding. This research falls under the categories of NS2 Based Thesis Projects and Wireless Research Based Projects, with a specific focus on Wireless security as a subcategory.
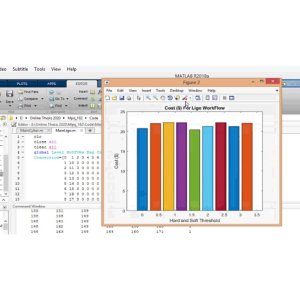
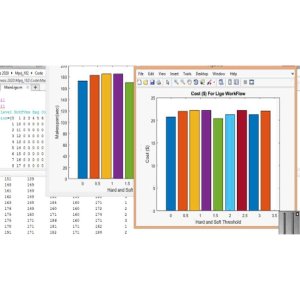
The project utilizes NS-2 software for simulation and analysis of the proposed methods.
Application Area for Industry
This project on detecting and mitigating Vampire attacks in wireless ad-hoc sensor networks has the potential to be applied across various industrial sectors such as the IoT industry, smart cities, healthcare, and industrial automation. In the IoT industry, where wireless sensor networks are extensively used for monitoring and controlling connected devices, the threat of Vampire attacks can disrupt critical communication systems. In smart cities, the use of wireless sensor networks for various applications such as traffic management, waste management, and energy monitoring can be impacted by these attacks. In healthcare, where wireless sensor networks are utilized for patient monitoring and medical device communication, ensuring the security and reliability of data transmission is paramount. Similarly, in industrial automation, where wireless sensor networks are employed for process monitoring and control, protecting against Vampire attacks is crucial to prevent disruptions and ensure operational efficiency.
By implementing the proposed solutions to detect and mitigate Vampire attacks in wireless ad-hoc sensor networks, industries can address specific challenges such as ensuring the stability and functionality of the networks, protecting data integrity, and mitigating the risks posed by malicious insiders. The benefits of implementing these solutions include safeguarding against disruptions caused by energy depletion due to Vampire attacks, enhancing network security and reliability, and maintaining the overall performance of the networks. As industries increasingly rely on wireless ad-hoc sensor networks for various applications, developing effective strategies to counteract Vampire attacks is essential to safeguarding critical infrastructure and ensuring seamless operations across different industrial domains.
Application Area for Academics
The proposed project on addressing Vampire attacks in wireless ad-hoc sensor networks offers a valuable opportunity for MTech and PHD students to engage in innovative research methods and data analysis within the realm of wireless security. The increasing prevalence of such attacks presents a pressing challenge that requires sophisticated solutions to ensure the stability and reliability of data transmission. By focusing on the depletion of nodes' battery power by malicious entities at the routing protocol layer, researchers can explore the vulnerabilities of existing protocols and develop effective mitigation strategies. This project, categorized as NS2 Based Thesis Projects and Wireless Research Based Projects, provides a platform for students to conduct simulations, analyze data, and propose novel solutions to combat Vampire attacks. By leveraging the NS-2 software for simulation purposes, students can explore the effectiveness of their proposed methods and contribute to the advancement of wireless security in the research domain.
With its relevance in addressing a critical issue in wireless ad-hoc sensor networks, this project offers a rich foundation for MTech students and PHD scholars to pursue impactful research for their dissertation, Thesis, or research papers. Furthermore, researchers can use the code and literature from this project to expand their knowledge base and explore future scope in the field of wireless security.
Keywords
Vampire attacks, wireless ad-hoc sensor networks, battery power depletion, malicious insiders, data transmission integrity, protocol compliance, energy consumption, detection and mitigation, network performance, security and reliability, routing protocol layer, destructive actions, proof-of-concept protocol, data packet forwarding, NS2 software, simulation and analysis, Wireless security, NS2 Based Thesis Projects, Wireless Research Based Projects.
| Shipping Cost |
|
No reviews found!















No comments found for this product. Be the first to comment!