Wireless Network Spoofing Attack Detection and Localization using RSS and SVM
Problem Definition
Problem Description: Wireless networks are vulnerable to spoofing attacks, where malicious attackers can impersonate legitimate nodes and disrupt network communication. These attacks can hinder the performance of the network and compromise the security of the data being transmitted. Current cryptographic authentication approaches may not be sufficient to accurately detect and localize multiple spoofing attackers, leading to overhead requirements and inefficiencies in network operation. There is a need for a more effective method to detect and localize multiple spoofing attackers in wireless networks, without imposing excessive overhead on the system. It is crucial to develop a system that can accurately determine the number of attackers and pinpoint their locations within the network, in order to prevent and mitigate the impact of these malicious activities on network performance and security.
Proposed Work
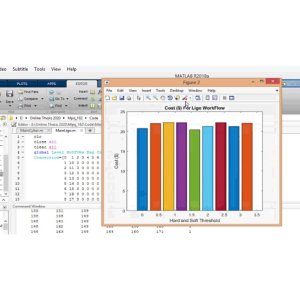
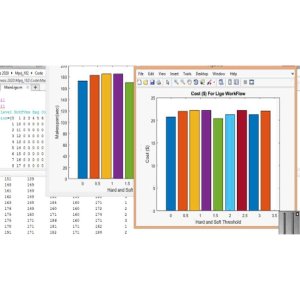
The project titled "Detection and Localization of Multiple Spoofing Attackers in Wireless Networks" aims to address the issue of spoofing attacks in wireless networks through the use of spatial correlation of the received signal strength (RSS) from nodes in the network. By developing cluster head mechanisms and utilizing Support Vector Machines (SVM), the method is able to accurately determine the number of attackers present in the network. Additionally, an integrated detection and localization system is created to pinpoint the exact position of the multiple attackers. This research falls under the categories of NS2 Based Thesis Projects and Wireless Research Based Projects, with specific relevance to the subcategories of Wireless Security and WSN Based Projects. The proposed method is evaluated through testing in real office buildings using both 802.
11 (Wi-Fi) and 802.15.4 (ZigBee) networks, showcasing its effectiveness in detecting and localizing spoofing attacks. The software used for implementation includes NS2 and SVM algorithms.
Application Area for Industry
The project on "Detection and Localization of Multiple Spoofing Attackers in Wireless Networks" can be applied in various industrial sectors such as the telecommunications industry, the cybersecurity sector, and the Internet of Things (IoT) domain. In the telecommunications industry, where wireless networks are widely used for communication, the proposed solutions can help in safeguarding network integrity and ensuring secure data transmission. In the cybersecurity sector, the system can assist in enhancing network security measures by accurately detecting and localizing spoofing attacks, thereby reducing vulnerabilities and mitigating potential risks. In the IoT domain, where a multitude of devices are connected wirelessly, the project's methods can be instrumental in maintaining the integrity and security of interconnected systems.
Specific challenges that industries face, such as maintaining network performance and data security in the face of increasingly sophisticated cyber threats, can be addressed by implementing the proposed solutions.
By accurately determining the number of attackers and pinpointing their locations within the network, industries can proactively prevent and mitigate the impact of malicious activities on network performance and security. The benefits of implementing these solutions include improved network reliability, enhanced data protection, and reduced operational inefficiencies due to the prevention of disruptions caused by spoofing attacks. Overall, the project offers a holistic approach to addressing the vulnerabilities associated with wireless networks and provides a robust system for detecting and localizing spoofing attackers in various industrial domains.
Application Area for Academics
The proposed project on "Detection and Localization of Multiple Spoofing Attackers in Wireless Networks" holds great potential for MTech and PhD students in the field of wireless networks, particularly in the areas of wireless security and WSN-based projects. This research tackles the critical issue of spoofing attacks in wireless networks by utilizing spatial correlation of the received signal strength and employing cluster head mechanisms with Support Vector Machines (SVM) for accurate detection and localization of multiple attackers. MTech and PhD students can use this project for innovative research methods, simulations, and data analysis in their dissertations, theses, or research papers. By utilizing NS2 and SVM algorithms for implementation, students can explore the effectiveness of the proposed method in real-world scenarios, such as office buildings with 802.11 (Wi-Fi) and 802.
15.4 (ZigBee) networks. This project provides a valuable resource for researchers to enhance network security and performance, as well as contribute to advancements in the field of wireless communication. The future scope of this project includes further optimization of the detection and localization system, as well as potential integration with other security mechanisms to combat evolving cyber threats in wireless networks.
Keywords
Wireless networks, spoofing attacks, malicious attackers, network communication, performance, security, cryptographic authentication, detect attackers, localize attackers, wireless security, WSN, NS2, SVM, cluster head mechanisms, Support Vector Machines, spatial correlation, received signal strength, network performance, network security, real office buildings, Wi-Fi networks, ZigBee networks, NS2 algorithms, SVM algorithms, detection system, localization system.
| Shipping Cost |
|
No reviews found!















No comments found for this product. Be the first to comment!