Enhanced Security Scheme for Wireless Sensor Networks with Mobile Sinks
Problem Definition
PROBLEM DESCRIPTION: The existing key pre-distribution schemes used for establishing and authenticating keys between sensor nodes and mobile sinks in wireless sensor networks are vulnerable to security threats. Attackers can exploit these schemes by capturing a small fraction of nodes to obtain a large number of keys, compromising the overall network security. Additionally, the deployment of a replicated mobile sink preloaded with compromised keys further exacerbates the security challenges in the network. This poses a significant risk to the integrity and confidentiality of the data collected and transmitted by the mobile sinks in various applications such as data accumulation, sensors reprogramming, and compromised node detection in wireless sensor networks. Addressing these security vulnerabilities is critical to ensuring the secure operation of the Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks project.
Proposed Work
The proposed work titled "The Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks" focuses on addressing the security challenges in wireless sensor networks (WSN) where mobile sinks play a crucial role in tasks such as data accumulation, localized sensor reprogramming, and detection and revocation of compromised nodes. The existing key pre-distribution schemes used for key establishment and authentication between sensor nodes and mobile sinks have been found to be vulnerable to attacks, as attackers can capture a small fraction of nodes to obtain a large number of keys. This poses significant security risks, as deploying a replicated mobile sink preloaded with compromised keys can allow attackers to gain control of the network. This project falls under the categories of NS2 Based Thesis Projects and Wireless Research Based Projects, with subcategories including Mobile Computing Thesis, Wireless Security, and WSN Based Projects. The research will utilize software such as NS2 for simulation and analysis.
Application Area for Industry
The Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks project has the potential to be applied in various industrial sectors such as smart manufacturing, agriculture, healthcare, and environmental monitoring. In smart manufacturing, the project's proposed solutions can help secure the communication and data transfer in industrial IoT devices and sensors, ensuring the integrity and confidentiality of sensitive information. In agriculture, the project can be utilized to protect data collected from field sensors and drones, preventing unauthorized access and manipulation. In healthcare, the project's security measures can safeguard patient data transmitted from wearable devices and medical sensors, maintaining privacy and compliance with healthcare regulations. Lastly, in environmental monitoring, the project can be used to secure data gathered from sensors deployed in remote locations, mitigating the risk of data tampering and unauthorized access.
By implementing the Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks, industries can address specific challenges related to securing sensitive data and ensuring the safe operation of interconnected devices, ultimately benefiting from enhanced security, reliability, and trust in their systems.
Application Area for Academics
The proposed project on "The Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks" presents a significant opportunity for MTech and PhD students to engage in cutting-edge research in the field of wireless sensor networks. By addressing the security vulnerabilities in key pre-distribution schemes for sensor nodes and mobile sinks, students can explore innovative research methods, simulations, and data analysis techniques for their dissertations, theses, or research papers. This project is particularly relevant for students specializing in Mobile Computing Thesis, Wireless Security, and WSN Based Projects, as it offers a hands-on approach to understanding and improving the security of wireless sensor networks with mobile sinks. By utilizing software such as NS2 for simulation and analysis, students can explore different scenarios, evaluate the effectiveness of the proposed security scheme, and generate valuable insights for their research. The code and literature from this project can serve as a valuable resource for researchers and students in the field, providing a foundation for further exploration and potential advancements in wireless security and network protocols.
Looking ahead, the future scope of this research includes exploring advanced encryption techniques, enhancing key management protocols, and integrating machine learning algorithms for anomaly detection in wireless sensor networks with mobile sinks.
Keywords
key pre-distribution schemes, wireless sensor networks, mobile sinks, security threats, network security, compromised keys, data collection, data transmission, Three-Tier Security Scheme, proposed work, security challenges, WSN, sensor nodes, authentication, key establishment, attackers, security vulnerabilities, replicated mobile sink, data accumulation, sensor reprogramming, compromised node detection, NS2, simulation, analysis, Mobile Computing Thesis, Wireless Security, WSN Based Projects, Wireless Research Based Projects, NS2 Based Thesis Projects.
| Shipping Cost |
|
No reviews found!









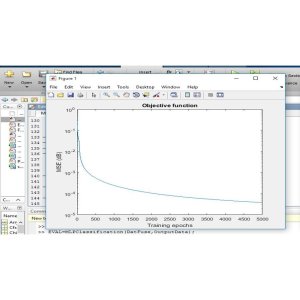
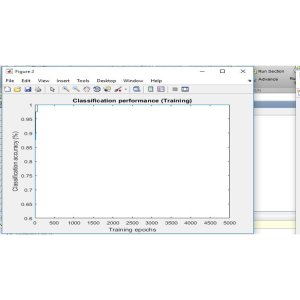

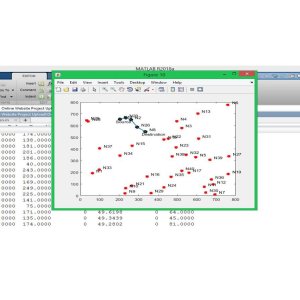
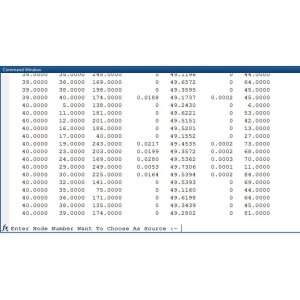



No comments found for this product. Be the first to comment!